Restricted Data
Restricted data contain sensitive information (i.e., information that can cause potential cause harm if revealed) or information that enables the potential identification of respondents through inference. Data may also be restricted because of confidentially promises or proprietariness.
Examples of sensitive information are reports of sexual behavior, criminal history, drug use, mental health history, HIV status, information collected from minors, or other materials that warrant extra discretion.
At DSDR, the identities of research subjects are confidential. DSDR and its data providers take the confidentiality of research subjects seriously. DSDR reviews all deposited datasets to assess disclosure risk and implements protocols to prevent the re-identification of research subjects.
Identifying Studies with Restricted Data
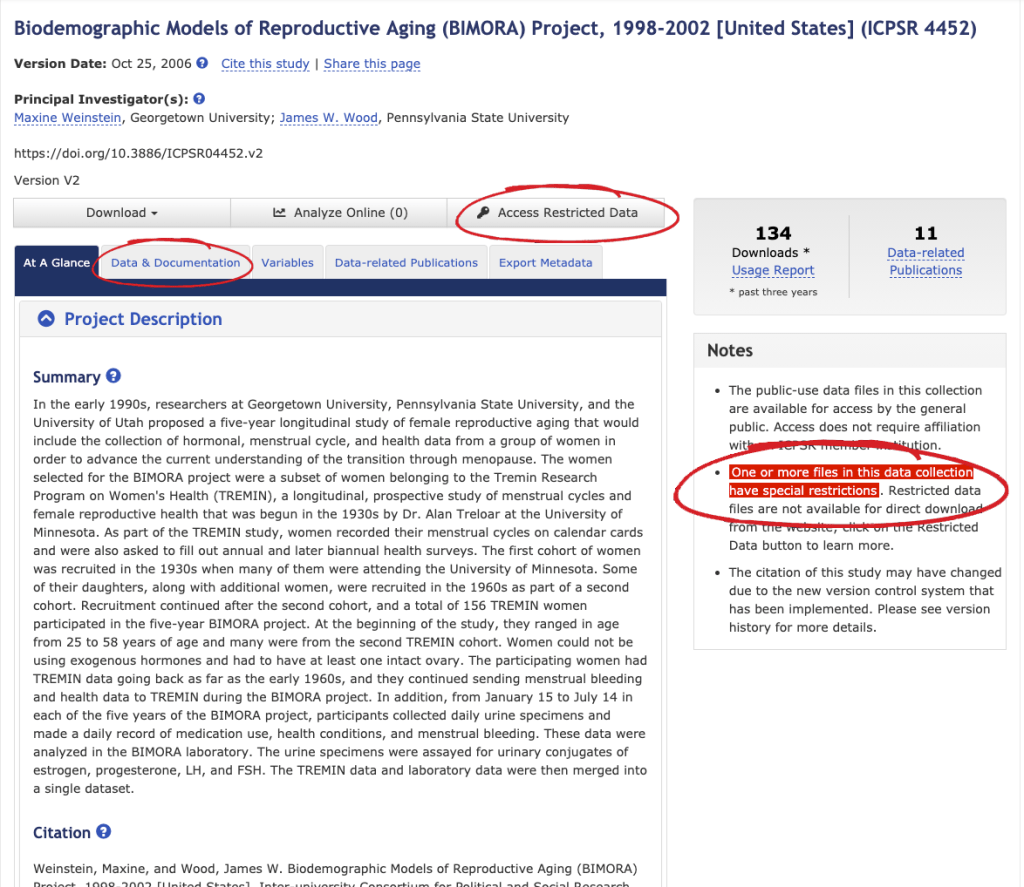
As shown below, data restrictions are indicated in three areas on the study home page:
- Notes section: Includes information on the restriction(s) for the study.
- Data & Documentation tab: Restricted datasets will not have a download button for data under the Download column. Documentation may still be available for download.
- Access Restricted Data button: This button will only display for studies containing restricted data. Selecting this tab results in a pop-up box with information on the available access options.
Applying for Access to Restricted Data
DSDR uses three methods to provide access to restricted data:
- Secure Download: Data are encrypted and delivered via download to a researcher. The researcher must destroy any copies of the data at the completion of the project.
- Electronically via the ICPSR Virtual Data Enclave (VDE): Data remain on the ICPSR file servers and are accessed and analyzed by the researcher virtually. DSDR staff review output for disclosure risk prior to transferring results to the researcher. The VDE facilitates collaboration by allowing members of the project team to connect to the server from their separate, approved locations.
- In person via the ICPSR Physical Data Enclave (PDE): A small number of DSDR studies are only accessible on-site at ICPSR’s offices in Ann Arbor, MI. Data in the PDE typically contain highly sensitive, personal information or data from protected populations. To analyze data stored in the PDE, approved researchers must travel to ICPSR. DSDR staff review output for disclosure risk prior to approving files for removal from the PDE.
| [empty] | Secure Download | Virtual Data Enclave (VDE) | Physical Data Enclave (PDE) |
|---|---|---|---|
Number of Access Locations | Usually one approved location | Multiple approved locations | One (ICPSR Physical Data Enclave in Perry Building) |
Internet Access Permitted | No | Encrypted connections to the VDE; Blocked from within VDE | No |
Output Vetting Performed by | Approved Researcher(s) | DSDR Staff | DSDR Staff |
Cross-Institution Collaboration | Separate Agreements; Can share/discuss vetted results | Specifically designed for this collaboration – Separate Agreements; Same Project Space accessible by all researchers | Only share/discuss approved output after leaving the PDE |
Software Available | Specific to Researcher/Institution | Windows desktop with major statistical packages and Microsoft Suite. Additional information | Windows computer with the Microsoft Office Suite and the SPSS, SAS, and Stata statistical packages. Arrangements must be made in advance for other software |
Additional Information |
Information about applying for access to restricted data is available on the home page for each study. Application requirements may vary by study as well as the method of access (e.g., secure dissemination). Standard requirements include the following:
- Your institution must classify and confirm you as a Principal Investigator (PI), eligible to lead a research project
- Most agreements require a terminal degree (e.g., PhD, MD, JD, DrPH). Other researchers, including graduate students, may obtain access to the data if they are supervised by a PI-eligible approved researcher.
- Restricted Data Use Agreement (R-DUA) signed by a legal representative of the receiving institution and the PI
- Proof of IRB review
- Confidentiality pledges signed by the PI and each research staff (anyone who can access the data)
- Confidential Data Security Plan(s) affirmed by the PI and each research staff
- Project description explaining why the data are needed for the research